Despite endless hacks and stolen data, millions of people are still protecting their digital lives with passwords so predictable that hackers barely have to try.
A new analysis from Comparitech, which reviewed more than 2 billion leaked passwords from 2025, reveals that weak and easy-to-guess passwords remain the default for far too many users. Among the most common offenders: “Minecraft,” “qwerty,” and regional favorites such as “India@123.”
Even after years of awareness campaigns, the same tired combinations, “123456,” “password,” “admin,” and “1234”, continue to dominate login databases. According to the study, 38.6% of the top 1,000 passwords still contain “123,” while just 3.2% stretch beyond 16 characters, a threshold generally considered more secure.
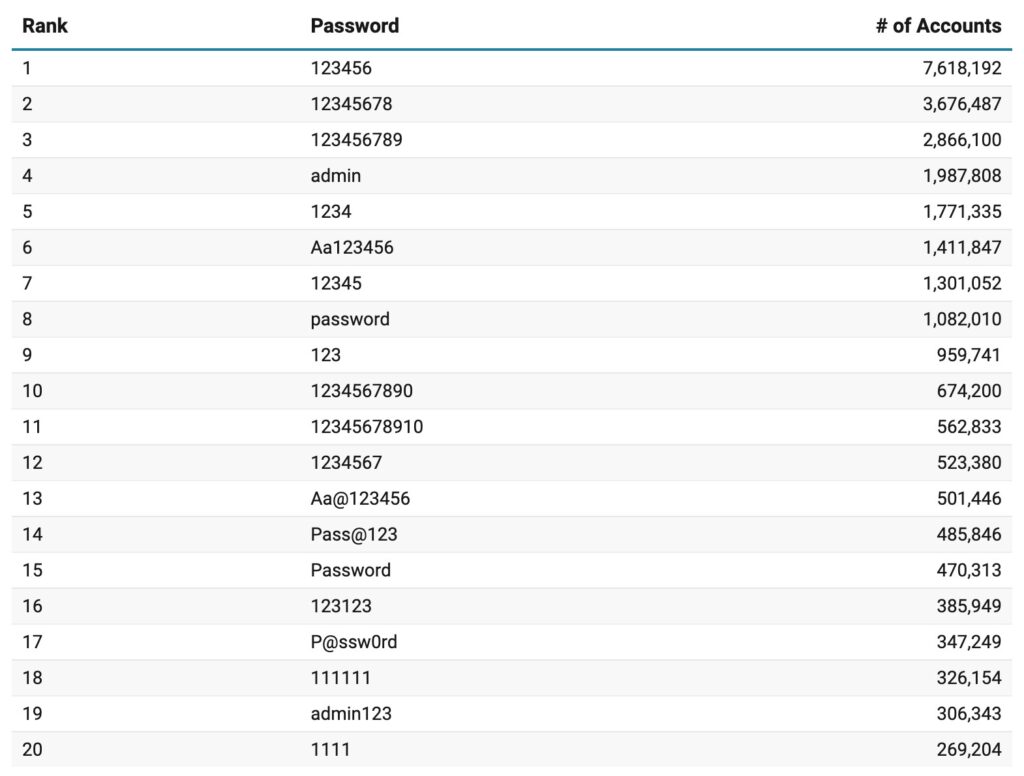
The Same Old Mistake
These findings underscore an uncomfortable truth: weak passwords are still the easiest entry point for cybercriminals. Brute-force attacks and credential-stuffing, when hackers reuse stolen login details from one site to access another, remain wildly effective because too many people rely on short, predictable words.
And it’s not just individuals at risk. Recycled passwords across multiple accounts create a chain reaction of vulnerability that can compromise entire systems when a single platform is breached.
Why It Matters
In today’s connected world, password hygiene is often the only line of defense between private data and a bad actor with a simple script. Whether you’re checking email, shopping online, or managing a company bank account, a password like “123456” practically hands over the keys.
Short passwords can be cracked in seconds by automated tools. Even more complex ones can fail if reused across services. The rule of thumb hasn’t changed: length, randomness, and uniqueness remain the best protection.
What You Can Do Right Now
If you recognize any of your go-to passwords on this list, change them immediately. Aim for at least 12 characters, mixing uppercase and lowercase letters, numbers, and special symbols.
Don’t rely on birthdays, pet names, or simple sequences, they’re the first things hackers test. Wherever possible, enable two-factor authentication (2FA) to create an extra security layer.
And if managing dozens of unique passwords sounds overwhelming, consider using a password manager or switching to passkeys, which generate secure, device-verified logins that don’t rely on memorization at all.